Tea App Leak Shows Digital ID Verification Exposes Your Data To Potential Abuse | Another Reason To Resist Digital ID

Tea App Leak Shows Why UK’s Digital ID Age Verification Laws are Dangerous
The online "safety" act is actually a threat.
ReclaimTheNet.org
Christina Maas
The UK’s Online “Safety” Act, legislation marketed as a safety net for children, was rolled out with all the foresight of a toddler launching a space program. Now, any site hosting “potentially harmful” content could be required to collect real-world ID, face scans, or official documents from users.
What could go wrong? Ask Tea, the women-centric dating gossip app that went viral by promising empowerment, then faceplanted into one of the most dangerous data breaches of the year. Their Firebase server, housing tens of thousands of selfies and government-issued IDs, was left wide open to anyone with a link.
This is the real-world consequence of lawmakers selling digital ID mandates as a solution to online harm: private companies getting access to sensitive personal data with all the discretion of a parade float, and then dropping it into the laps of the entire internet.
Let’s pause for a moment and appreciate the cosmic genius it takes to build an app allegedly designed to protect women, and then expose all of their private data to the world with the finesse of a first-time hacker copying a URL.
Tea, the dating app that rocketed to the top of the App Store by selling anonymity, safety, and empowerment, before face-planting into the Firebase server floor, spraying driver’s licenses and selfies like a busted confetti cannon.
If you missed it, here’s the elevator pitch from the seventh circle of infosec hell: Tea lets women upload photos, names, and backstories of men they’re dating (or avoiding), tagging them as “green flags” or “red flags” like they’re judging a homecoming parade.
This was already a privacy demolition derby waiting to happen. But Tea wasn’t satisfied with sketchy crowdsourced accusations and anonymous callouts; it had a bigger goal: making sure only verified women could participate. And how do you verify womanhood in the 21st century? Naturally, you demand a selfie and a government-issued ID. Nothing says “safe space” like giving your face and passport to a buzzy gossip app run by people who store it in a publicly accessible Firebase bucket. No login. No password. No shame.
The data leak erupted. Users on 4chan stumbled across the open database and wasted no time slurping up tens of thousands of selfies, driver’s licenses, and even private messages; no encryption, no metadata scrubbing. Some uploads still contained geolocation data, meaning anyone who clicked “submit” had essentially handed over a real-time breadcrumb trail to their front door.

The fallout was immediate. At least one of the IDs allegedly belonged to a Department of Defense employee, according to social media posts that are now circulating with the gleeful schadenfreude of digital voyeurs.
Tea scrambled out a statement at 6:44 AM on July 25, claiming the breach affected a “legacy system” with data from “over two years ago.”
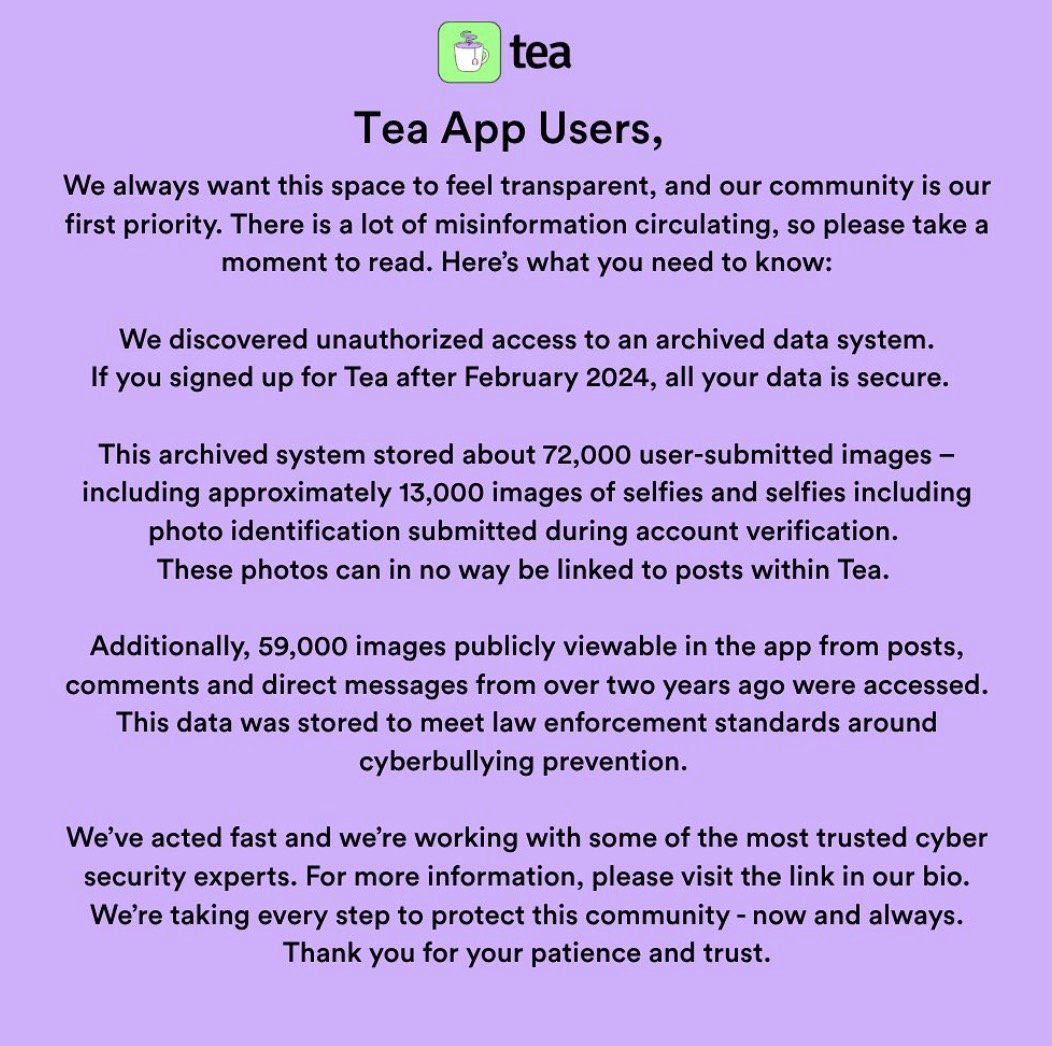
Of course, Tea’s entire pitch to women was that it created a safer dating ecosystem by weeding out imposters and creeps through ID-based gatekeeping. But as it turns out, the real danger wasn’t the guy with the “red flag” tag. It was the company itself that built a high-value honeypot of sensitive personal information and then forgot to put a lid on it.
Digital IDs: The Snake Oil of Online Safety
Tea’s disaster is less a standalone embarrassment and more like a blinking red billboard advertising the idiocy of digital ID verification as a privacy safeguard. The idea sounds good in committee rooms and on tech conference stages: require people to upload real ID to confirm their identity online, and magically the trolls vanish, the bots disintegrate, and your app becomes a utopia of civil discourse and polite dating.
Except no. What you actually get is a surveillance regime that centralizes priceless identity data in systems so brittle they buckle under the weight of a URL request. Tea didn’t suffer a breach because of a masterful hack; it got busted because it left the front door open and taped the key to the welcome mat.
Mistakes always happen, and hacks are common, which is why platforms should be collecting as little data as possible, and digital ID requirements are a dangerous idea.
And it’s not like this practice is going away. It’s being enshrined into law. The UK’s shiny new Online Safety Act is the sort of performative legislation that gives regulators a warm feeling without the burden of logic.
Touted as a noble effort to protect children and users from online harms, it mandates sweeping age verification that essentially forces everyone; kids, adults, and unlucky DOD employees, to hand over their ID to participate in the most mundane corners of the internet.
Tea’s breach is a preview. The Online Safety Act could easily turn every minor app and niche site into a low-rent surveillance node, warehousing ID scans and facial data with about the same level of sophistication Tea showed.
Even massive platforms with armies of security engineers struggle to keep this kind of data locked down. Expecting cash-strapped startups and novelty apps to suddenly develop airtight, military-grade data infrastructure is like giving a toddler a flamethrower and hoping for landscaping.
The defenders of digital ID verification like to use words like “trust,” “protection,” and “authenticity.” What they don’t mention is what happens when things go wrong. IDs are lifetime access tokens to your real-world identity. You can’t revoke your face. You can’t replace your Social Security number every time a startup forgets to set its permissions.
But forget logic. These verification schemes are spreading faster than a mid-pandemic meme. Facial recognition, document scans, and biometric markers, because apparently, the only way to prevent harm is to turn every user into a government file. Meanwhile, the systems behind the curtain are leaky, opaque, and utterly indifferent to what happens once your data is out in the wild.
The policy has social costs, too. For whistleblowers, activists, abuse survivors, or anyone who depends on anonymity, being forced to submit ID in order to access information or express themselves online is the digital equivalent of tagging their house with a GPS marker.
This is the chilling effect built into the bones of legislation like the Online Safety Act. Lawmakers are trading constitutional principles for press-release optics, and users are stuck in a reality where privacy is painted as a threat to safety instead of its foundation.
Let’s kill the fantasy that this is a necessary tradeoff, that if you want to keep kids safe online, you have to install a digital checkpoint at every login screen. That you can’t combat abuse without building a panopticon.
The truth is, most of these ID collection schemes offer security theater, not actual security. They displace trust from the users and place it into a black box system with no accountability. When the system fails, as Tea’s has, it’s the users who pay. With their data and their safety.
Tea collected 72,000 images, selfies, and IDs, and dumped them into an open Firebase bucket like it was saving screenshots from a group chat. If this is what a platform that says it’s to protect women does with sensitive data, what should we expect from platforms that don’t even pretend to care?
Despite the fireball of press coverage and outraged social media posts, Tea hasn’t been banned. The app’s pages on the App Store and Google Play are still live. Its rating hasn’t cratered. No executives have resigned. No regulators have swooped in.
The message to other platforms is clear: you can screw this up in the most obvious, humiliating, and dangerous way possible, and nothing will really happen.
Meanwhile, governments are accelerating their push toward mandatory digital identity checks. It’s a future built on delusion. The infrastructure doesn’t exist. The trust isn’t earned. And the cost, as the Tea breach makes depressingly clear, is permanent.
So don’t upload your passport to join a chat room. Don’t submit a face scan to access a site. Don’t trust that trendy app founded last year with your biometric data.
Because once your face, name, and ID are out there, they’re not coming back. And when the next Tea-style leak hits, and it will, it won’t be an anomaly. It’ll be dangerous policy in action.
Original Article: https://reclaimthenet.org/tea-app-leak

Comments ()